top
of page

IP Addressing
Internet Protocol (IP) addressing
is based around four byte addressing. Each byte is referred to as an octet,
since it consists of eight bits. In hexadecimal the values for eight bits
(a byte) can be represented in two digits (00 to FF).
IP uses classes of networks to
determine the nature of the addressing. The addressing scheme dictates that
up to the initial four bits of the first byte are used to determine the class
of the network (see the diagram below). The remainder of the bits are used
to actually address the actual host in a network. There are four classes of
network A, B, C, & D.
Class |
1st
byte |
2nd
byte |
3rd
byte |
4th
byte |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A |
|
netid |
hostid |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
B |
1 |
0 |
netid |
hostid |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
C |
1 |
1 |
0 |
netid |
hostid |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
D |
1 |
1 |
1 |
0 |
multicast
address |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The table below shows the IP addresses
in base ten and binary for each of the four classes of networks. Also shown
are the number of networks and the number of hosts supported on each type
of network. Class D network addresses are reserved for multicasting.
Class |
Address
Range |
Number
of
Networks |
Number
of
Hosts |
| base-10 |
binary |
| start |
finish |
start |
finish |
|
A |
1.0.0.0
|
126.0.0.0 |
00000001.
00000000.
00000000.
00000000 |
01111110.
00000000.
00000000.
00000000 |
126 |
16777214 |
|
B |
127.1.0.0 |
191.254.0.0 |
01111111.
00000001.
00000000.
00000000 |
10111111.
11111110.
00000000.
00000000 |
16384 |
65534 |
|
C |
192.0.0.0 |
192.233.255.254 |
11000000.
00000000.
00000000.
00000000 |
11000000.
11101001.
11111111.
11111110 |
2097151 |
254 |
|
D |
233.0.0.0 |
255.0.0.0 |
11101001.
00000000.
00000000.
00000000 |
11111111.
00000000.
00000000.
00000000 |
n/a |
n/a |
top
of page

IP and DNS Addressing
The IP addresses have corresponding domain name services
(DNS) addresses. The DNS names are based on names that are much easier for
people to remember than the four sets of three digits that make up an IP address
(in base-10). However there are no rules linking the two systems, the DNS
system converts from one to the other simply by looking-up the correspondence
in a table.
Originally when there was just
the ARPANET, all computers had a list of all hosts and all the corresponding
IP addresses. Today this would be too large for any one system to hold. So
today the system is distributed among many machines. Addresses that are not
known to a local gateway are forwarded to another, until a machine is found
that can identify it. The DNS naming system is divided into name spaces called
zones. The zones allow for a directed searching for a DNS resolution.
top
of page

The Four Layer TCP/IP Model
In some textbooks and online resources
a four layer network model is used to describe the workings of TCP/IP. The
four layer model simplifies many of the layers used in the OSI model, making
it easier to understand than the OSI model. The four layer model incorporates
the physical and data-link layers in the first layer (called the network access
layer), the network layer in layer two (Internet layer), the transport layer
in layer 3 and the application, presentation and session layers in layer four
(application layer).
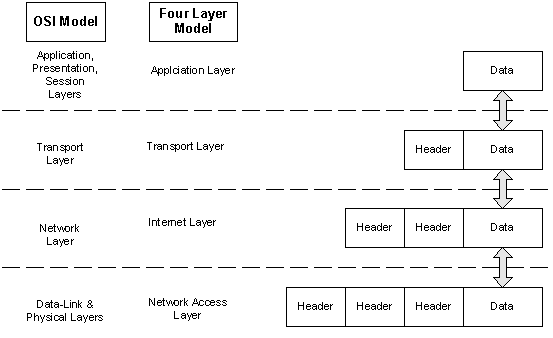
Here we will focus on TCP/IP using
the OSI model as this is the more widely used model and we can use TCP/IP
as an example of how to use the OSI model as a tool for understanding the
functioning of network protocols. But using the diagram above you should be
able to understand how TCP/IP works both from the perspective of the four
layer TCP/IP model and the seven layer OSI model. The four layer model is
widely known with regards to TCP/IP and is therefore a good thing to know.
top
of page

The Workings Of TCP/IP
First of all it is worthwhile noting where the protocols
of TCP and IP fit into the OSI model. As mentioned above they predominantly
fit into layers 3 and 4, the transport and network layers. However, the functions
of TCP are note restricted to just the transport layer.
top
of page

1. The Physical & Data-Link Layers
The physical (layer 1) & data-link (layer 2) layers
of the OSI model are not part of TCP/IP, since these work at higher layers.
However it is worthwhile considering them in order to understand how they
fit into the scheme.
Packaging Data: Frames
Data is packaged into packets
called frames. We will not consider the structure of the frames here.
It is worth noting that the network and transport layer also package the data.
Consequently there are layers of packaging.
MAC Addresses
Every piece of network hardware
has a unique hardware address, the Media-Access Control (MAC) address. This
number is fixed for hardware (such as Ethernet cards) at the factory. MAC
addresses consist of six hexadecimal numbers, each of two digits.
Address Resolution Protocol (ARP)
The address resolution protocol
(ARP) keeps track of the relationships between IP address (e.g. 192.168.0.11)
and the hardware addresses, represented by the MAC address (e.g. 00:D1:5E:23:73:A1).
top
of page

2. The Network Layer
Internet Protocol (IP) is the protocol in the TCP/IP system
that deals with the network layer, layer 3.
IP Routing
IP delivers the data to the address contained in the header
of each packet. If the IP address cannot be found locally, then the data is
passed on to t a local router or gateway that is able to forward it out of
the local network. This forwarding process continues, perhaps through many
routers, until it either reaches the correct IP address or is timed-out.
IP Data Packets: Datagrams
IP packages data into packets based on a 32-bit word. These
packets are called datagrams. The packets contain information about the protocol
being used and the destination address, as well as other information and the
data itself. The structure of an IP packet header is shown below.
| Version |
IHL |
Service
type |
Total Length of Datagram |
|
Identification |
Flags |
Fragmentation
offset |
|
Time
to live |
Protocol |
Header checksum |
|
Source Address |
|
Destination Address |
|
Options |
Padding |
|
Data,
starts here… |
|
|
|
|
|
|
|
Packet Re-assembly
On arriving at the destination, the IP packets may have
become fragmented. This can happen as different machines re-package the data
for forwarding. The IP software at the destination re-assembles the IP packets
before passing the data up to the TCP software, at the transport layer. The
protocol number contained in the datagram indicates which protocol is being
used at the transport layer. (It is often TCP but could easily be UDP or another
protocol.)
top
of page

3. The Transport Layer
At the transport layer TCP provides
connections between the source (host) and the destination. TCP provides reliable
connections, using hand-shaking to establish connections from point-to-point.
How TCP Creates a Connection
TCP uses a three-way hand-shake
to establish a connection, known as the SYN/ACK sequence.
- The host initiates by sending Synchronisation Sequence
Number (SYN) to the destination.
- The destination (target) responds with the SYN and
an Acknowledgement (ACK) bit set.
- The originating host sends its own Acknowledgement
(ACK) bit set and data transfer begins.
TCP Data Packets
TCP packages the data into packets based on 32-bit words.
The structure of a TCP packet header is shown below.
| Source Port |
Destination Port |
|
Sequence Number |
|
Acknowledgement Number |
|
Offset |
Reserved |
Flags |
Window |
|
Checksum |
Urgent Pointer |
|
Options |
Padding |
|
Data,
starts here… |
|
|
|
|
|
Looking at the diagram for the
four layer model, it is possible to see how the headers encapsulate the data
for each layer of protocol.
Passing Data up the OSI Model
Once data has been received by the TCP layer at the destination
and reassembled from the packets, it needs to passed up to the application
layer. In order to achieve this the port number is used. Different port numbers
are used for different applications. e.g. port 25 is used for SMTP
and port 80 for HTTP.
top
of page

4. Using the Data: The Application Layer & Port Numbers
The data is passed up through the layers until it reaches
the application or applications that
will use it. Data is targeted to the correct application using the port number.
Most common protocols and services have defined port numbers that are commonly
used. It is possible to reassign these and also assign port numbers for new
applications. Some services and port numbers typically used are shown below.
Service |
Port Number |
|
Echo |
7 |
|
FTP |
21 |
|
Telnet |
23 |
|
SMTP |
25 |
|
HTTP |
80 |

by
Matthew
Martin
top
of page

